At its annual conference on Oct. 19, Intel’s investment arm Intel Capital revealed it would be investing in 15 trailblazing technology startups from around the world.
Two of those are Israeli cybersecurity firms. The first, Alcide, is an innovative network security platform securing data centers against cyber attacks. The other, Intezer, uses a unique biological approach, inspired by the body’s immune system, to detect threats and malware.
Intezer uses concepts based on “DNA mapping” to detect code similarities in malware. This “DNA mapping approach to code” gives them a hand in providing unparalleled threat detection that accelerates the response of the enterprise being threatened.
The company has already had a hand in detecting these code similarities in massive cyber attacks, including WannaCry, Turla, NotPetya, and Bad Rabbit ransonware attacks.
SEE ALSO: Israeli Cybersecurity Firms Are In The Spotlight Again Following Global Ransomware ‘NotPetya’
“Intezer brings a unique solution to protect enterprises after the first line of defense was breached, especially in the realm of advanced targeted attacks which have become a global epidemic,” Magma Venture Partners Modi Rosen said in a statement. Tel Aviv’s Magma Venture Partners was one of the companies that contributed to an $8 million Series A investment in Intezer, led by Intel Capital.
“Intezer has developed the most advanced technology for detecting code-reuse, effectively performing ‘DNA mapping’ for software,” Intezer CEO Itai Tevet claims, “With this technology, we are able to identify every single piece of code running in the organization, enabling us to detect the most sophisticated cyber attacks and help security teams to respond immediately.”

Tevet founded the early stage venture with Roy Halevi and Alon Cohen in September 2015. Courtesy of Trend Micro
Other current investors in the funding round include Samsung NEXT and Alon Cohen, a co-founder of Intezer and a former CEO and founder of information security firm CyberArk Software.
What make Intezer’s technology stand out
Sign up for our free weekly newsletter
SubscribeIn May 2017, Intezer released its innovative Intezer Analyze solution, which detects cyber attacks that are likely invisible to other security tools. Made for file investigation and malware analysis, this online cloud services gives organizations a thorough understanding of a file by mapping its code at the DNA level. This rapidly accelerates the response to an attack. Tevet told BusinessWire that it can help you understand the details and origins of the suspected file while also showing code connections to malware, legitimate software, and libraries.
The global ransomware outbreak
Ransomware has hit countries like Russia, Ukraine, Turkey, and China with full force this year and Intezer was ready to pick up the pieces. Two of the largest attacks were the global WannaCry campaign in May and the NotPetya attack targeting Ukraine, but disrupted businesses worldwide. WannaCry and NotPetya were similar in that a hack used for WannaCry was also used for NotPetya, but NotPetya had extra powers were more potent than WannaCry, according to experts.
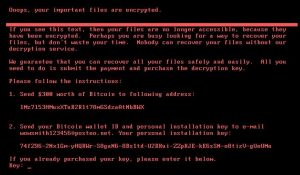
Petya Code – Hack Ransomware Malicious Worm Virus, via Geralt/Pixabay
Intezer’s Senior Security Researcher Jay Rosenberg has commented on the different ransomware in reports, analyses, and even tweets for the cybersecurity company. He also talked about Intezer’s use of Code Intelligence to track codes. While NotPetya hit the Cadbury chocolate factory in Australia, supermarkets in the Ukraine, India’s largest container port and more, “All of our customers were protected from the attack before inception, since it was detected by Intezer’s Code Intelligence technology,” he wrote in his report.
SEE ALSO: Keeping The Light On: Israeli Startups Protect Against Dire Cyber Attacks
Perhaps Intel recognized Intezer as one of 15 promising startups worth an investment because of their contributions in helping get rid of the newest ransomware threat Bad Rabbit. In a blog post published October 24, 2017, Rosenberg writes that reports have described the behavior of Bad Rabbit as being very similar to NotPetya. In fact, using their technology Intezer Analyze, the team has found code reuse from NotPetya through different binaries of Bad Rabbit. Eventually, through their tech, Intezer learned that there is only 13 percent code reuse between Bad Rabbit and NotPetya. In other words, Intezer’s recognition of the code reuse is what forces hackers that create malware to rewrite code and try again, which can be time consuming and not worth it in the long run.
Photos: Courtesy, Trend Micro, Geralt
Related posts

Editors’ & Readers’ Choice: 10 Favorite NoCamels Articles

Forward Facing: What Does The Future Hold For Israeli High-Tech?

Impact Innovation: Israeli Startups That Could Shape Our Future




Facebook comments