The Israeli military announced (Hebrew) on Sunday that it thwarted an attempt by the Palestinian terror group Hamas to gather intelligence on the Israel Defence Forces by hacking into soldiers’ phones using fake social media profiles of young women. The operation was part of a joint effort between the Military Intelligence Directorate (known as Aman), the IDF’s cyber defense unit, and the Shin bet (Israel’s internal security service), the Israeli military said.
The hack involved a catfishing operation (luring someone into a relationship or an interaction using fictional online personas) in which Hamas used at least six fabricated profiles of young women on social media channels including Facebook, Instagram, Whatsapp, and – for the first time, according to the IDF – Telegram. These were meant to lure soldiers into interacting with these personas and inadvertently downloading spyware that would allow access to their smartphones.
The IDF said part of its counter-operation involved taking out the Hamas servers used for the scheme.
TECH NEWS: US-Israeli Cyber Startup Unveils ‘Massive’ Telecom Hack Operation Linked To China
The military did not say exactly how many soldiers were affected but indicated that “several hundred” were believed to have been successfully targeted and were called in for a briefing and removal of the spyware.
Hamas created fake social media profiles, using photos including this one, in an attempt to hack the phones of IDF soldiers.
— Israel Defense Forces (@IDF) February 16, 2020
What Hamas didn’t know was that Israeli intelligence caught onto their plot, tracked the malware & downed Hamas’ hacking system.#CatfishCaught
This is at least the third known attempt by the Palestinian group to hack soldiers’ phones using similar methods. In 2017, the IDF first revealed that Hamas managed to hack into dozens of cellphones belonging to soldiers and officers in both active and reserve duty by posing as young women. Last year, Israel said it responded to a suspected hacking attack by bombing a building in the Gaza Strip, which Hamas rules, that served as a base for the hacking group. “HamasCyberHQ.exe has been removed,” the IDF tweeted in May alongside a picture of the targeted structure. Details of that particular attack, which the IDF called a “cyber offensive against Israeli targets,” were not disclosed.
In this latest attack, according to the military, Hamas operatives presented themselves as six different young women, ostensibly recent immigrants to Israel who did not speak Hebrew fluently. They also used hashtags and Israeli slang to increase their reach and made use of Facebook’s “intro” section to seem credible, according to Col. R (“Resh” in Hebrew), the IDF’s information security chief.
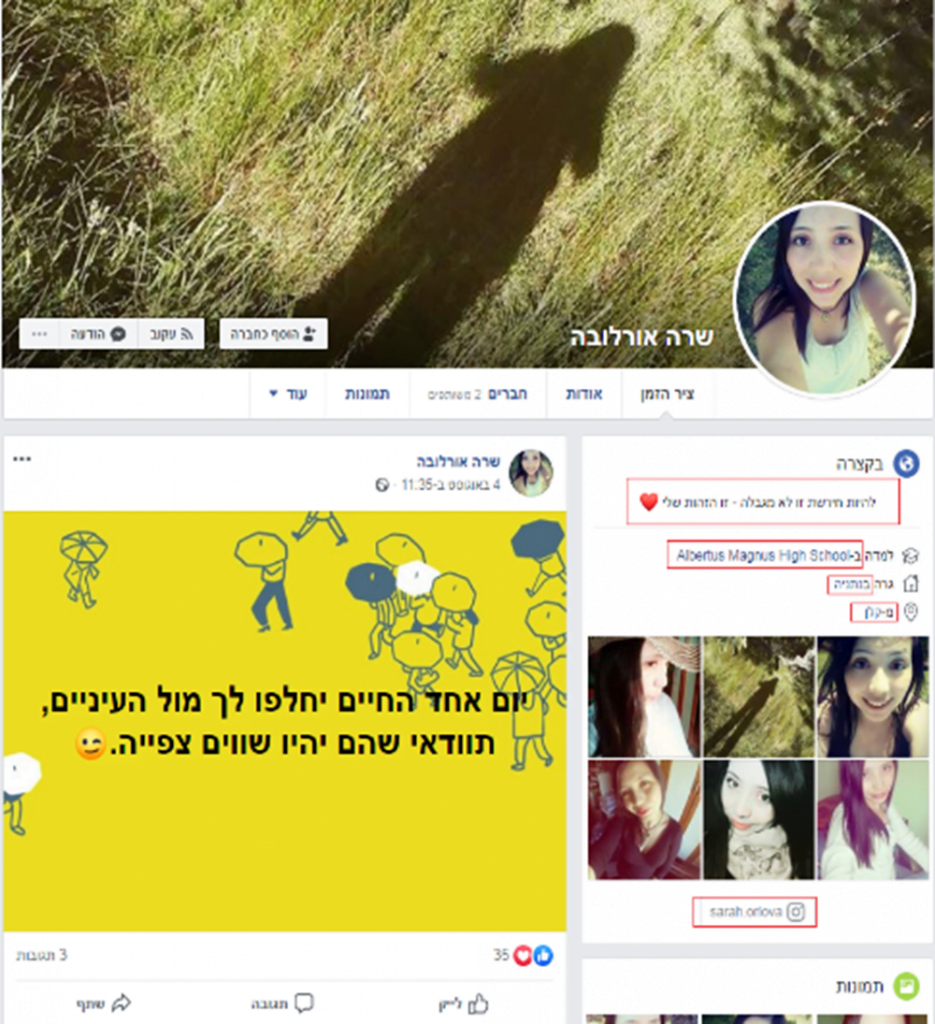
“Hamas edited the images of the personas to make it difficult to find their source and made sure to operate on multiple networks,” added R.
Once contact was made, the personas encouraged the targets to download one of three applications, promising to send pictures. Websites for these apps described them as a tool for sending and receiving pictures that are then wiped (similar to Snapchat).
The apps – which the IDF identified as Catch&See, ZatuApp, and GrixyApp – would infect the phones and allow access to the device once downloaded. The Hamas operatives could then transfer files, take pictures remotely, download and run additional files, collect contacts, phone IDs, and text messages and access GPS location.
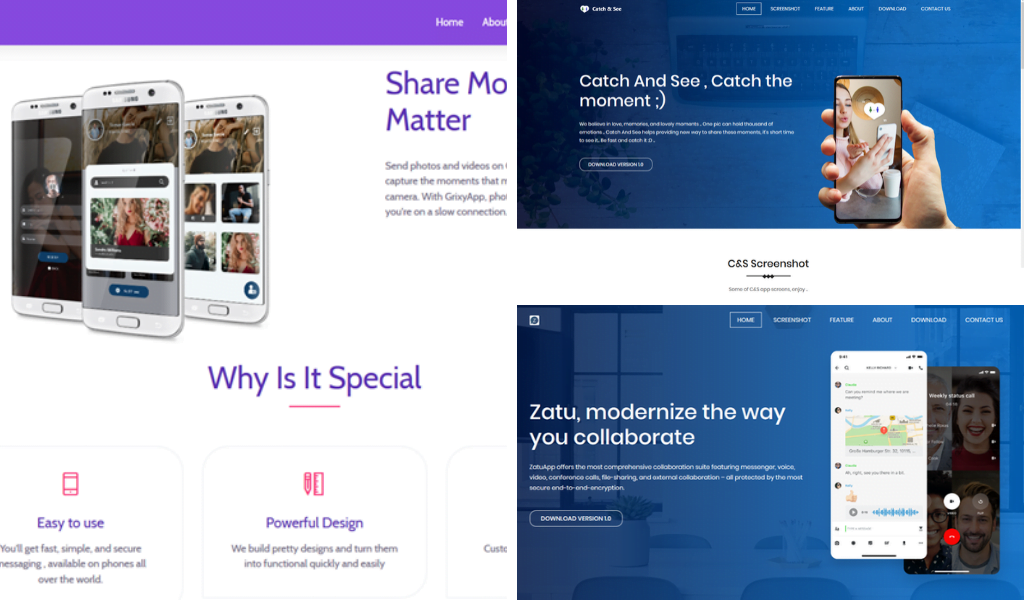
The personas would discourage calls or video chats by claiming to have hearing impairments. In some cases, voice notes bearing the voices of women saying “yes” or no” in Hebrew were sent to the soldiers to increase credibility, according to the military.
Sign up for our free weekly newsletter
SubscribeThe IDF said it the malware’s function was “high level and more sophisticated compared to the terrorist organization’s past infrastructure.”
The reach was also notable, according to the IDF which said that previous attacks targeted combat soldiers only but the latest one targeted a wider range of service members.
TECH NEWS: Facebook, WhatsApp Sue Israeli Cyber Intel Firm NSO Group Over Alleged Hacking Attack
The IDF said it caught on to the attack several months ago and began tracking the operation, in part, through one of the fake personas already identified in a previous cyber event. This knowledge was not disclosed at the time “in order to monitor Hamas’ technological infrastructure” and to identify further cyber activity against IDF soldiers.
R. said that the military assesses that was no substantial security damage. “In cases where it was identified that damage may occur – we acted immediately, R. said.
Levels of sophistication
The level of sophistication of a catfishing operation can be assessed in two ways, explains Lotem Guy, a cybersecurity expert and the VP Product at Cybereason, a US-Israeli cybersecurity firm that offers endpoint detection and response (EDR), next-generation antivirus (NGAV), and active monitoring services, through its Cyber Defense Platform.
“One is how much effort the attacker puts into appearing real. You can send a “you’ve won the lottery” message to someone or you can be more specific and target someone based on their likes and interests. And nowadays, you can know a lot about a person using social media and victims may not realize they are victims,” Guy tells NoCamels in a phone interview.
“The second question is ‘how sophisticated is the tech’? ‘What are you having people do’? In this case, you are forcing people to download an app that gives access to your phone,” he explains.
Hamas created these fake profiles and these apps for this operation and this is quite sophisticated, Guy says. Once downloaded, the apps appeared to be crashing but they were working, he went on, explaining how the attack worked.
“The victims expected to see some sort of dating app – and who knows, maybe Hamas will create a dating app at some point,'” he jokes.
Related posts

Editors’ & Readers’ Choice: 10 Favorite NoCamels Articles

Forward Facing: What Does The Future Hold For Israeli High-Tech?

Impact Innovation: Israeli Startups That Could Shape Our Future




Facebook comments