As Israel declared war on the Hamas terrorist organization that ruled Gaza in the aftermath of the heinous terror attack of October 7, a new front immediately opened up, with a huge wave of cyber strikes targeting the digital assets of Israeli government branches, businesses and institutions.
Israel has always been subject to large numbers of cyber attacks, but the level of aggression massively grew on that day, explains Ron Meyran, the head of cyber intelligence at Radware, a cybersecurity company in Tel Aviv.
“We can see a clear increase in cyber attacks against Israeli targets” since the start of the war, Meyran tells NoCamels, based on data the company collected from its own cloud services and the experiences of its clients.

In order to monitor these attacks and potential attacks, the company has infiltrated the channels of threat actors on the Telegram messaging platform, gathering intelligence on who their targets are, why they have chosen those organizations and how they plan to strike.
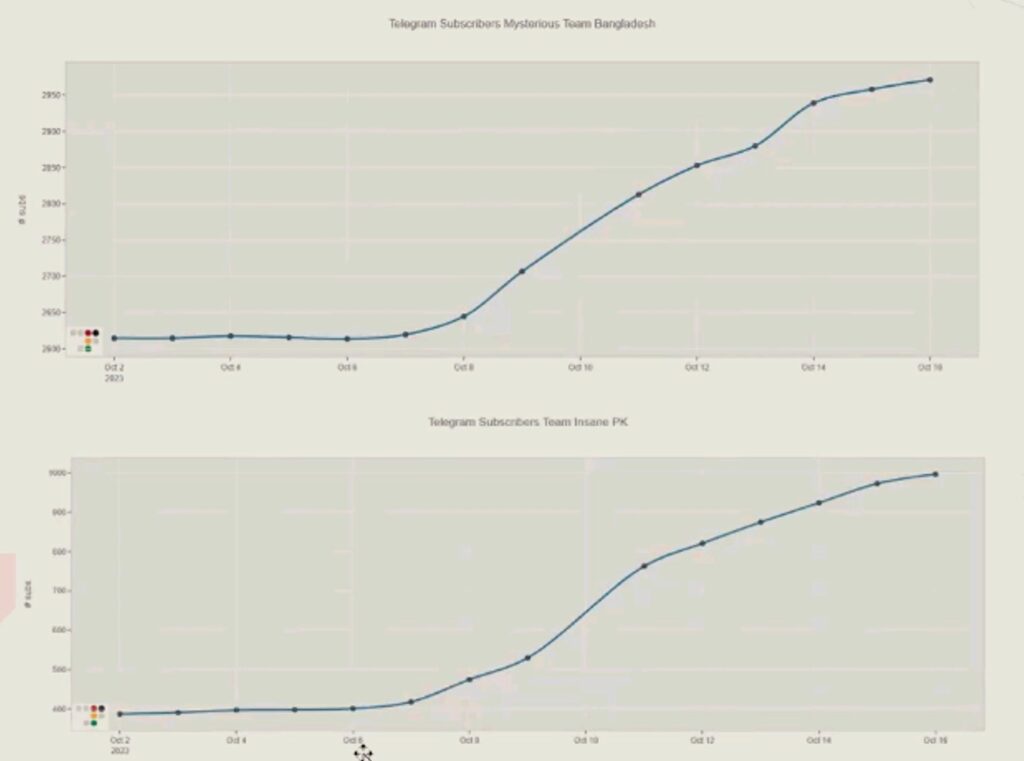
And as the number of attacks against Israel rose, these channels also saw a dramatic increase in followers since the Hamas massacre of 1,200 people.
“If each of these threat actors had several thousand followers, suddenly there was a clear rise – you see the number of followers jumping starting October 7,” Meyran says.
Those operating the channels create “collectives” of people who they train and provide tools in order to carry out cyberattacks, he explains.
The Radware team poses as willing participants of a collective in order to obtain access to these tools, which are then dissected by the company.
“We download these tools, we follow the instructions,” Meyran says. “We test the tools in the lab to see which vectors these tools are generating in order to then define protection rules against them.”
Potential strikes against Radware clients are handled by the company, he says, but any other Israeli organizations believed to be under threat are warned that they could be targeted.
Israel, he explains, is “by far” the most attacked country in the world, enduring three to four times more cyber attacks than the other countries who are also frequently targeted.
These countries include the US and India, as well Western nations such as Germany, Sweden and Finland, who are usually targeted by pro-Russian threat actors due to the conflict in Ukraine.
Russia is also behind some of the attacks on Israel, he says, primarily using a “well organized” pro-Russian hacker group called Killnet.
At first it was not clear to Radware why such a group, which the company believes is taking direction from Moscow, would suddenly begin targeting Israel. But then they started to see messages on Telegram quoting Russian President Vladimir Putin and the Russian media as saying that Israel is solely responsible for the current conflict and deserved to be attacked due to its support for Ukraine.
These Telegram messages included the Russian flag and the Palestinian flag together, he says.
Even so, Meyran explains, the attacks on Israel are mainly coming from religious threat actors in places such as Pakistan, Indonesia, Morocco and Bangladesh.
Sign up for our free weekly newsletter
Subscribe
And while such groups have always carried out cyber attacks in Israel, he points out that there is now evidence of them joining forces, which they had never done before.
Nonetheless, he says, there is no reason to believe there is one major organization or state sponsor controlling and guiding these religious groups.
Many of the strikes come in the form of distributed denial-of-service (DDoS) attacks, which are attempts to bring down a website or server by overwhelming it with huge amounts of traffic at the same time.
These DDoS attacks can bring down a website for a short period, Meyran says, and typically they are solely intended to cause disruption.
“The idea is to create chaos,” he explains, such as temporarily bringing down news websites, banking systems and even healthcare platforms. But while these attacks normally do not have far-reaching consequences, they can occasionally be used as cover for more pernicious assaults.
“While the IT system people and the security people are busy with the large attacks, which are very visible, there may be a few pockets that will try to penetrate or steal information or compromise applications which would go undetected or under the radar,” he says.
Other kinds of dangerous cyber attacks have included attempts to disable the Israel Defense Forces’ air raid sirens that warn people to take shelter from incoming rocket strikes from Gaza or Lebanon.
The attackers have managed to very briefly bring down the system both during this conflict and in previous ones, Meyran says. He points out, however, that this is not the only way the country warns of imminent rocket strikes.

The attackers have also targeted industrial control systems, including utilities such as power stations and water treatment plants, again with little success.
“From what I see they’re quite well protected,” Meyran says.
He warns, however, that the attacks are becoming more sophisticated, with hackers targeting application programming interfaces (APIs) – software that allows two or more programs to talk to one another – rather than the individual systems.
The heavy encryption used by the Telegram platform makes its channels notoriously hard to monitor or block, but Meyran believes this is an advantage.
“Why shut it down? If they shut it down, they simply will move to other channels,” he points out.
“This is a place where we can see what’s happening.”
Related posts

Editors’ & Readers’ Choice: 10 Favorite NoCamels Articles

Forward Facing: What Does The Future Hold For Israeli High-Tech?

Impact Innovation: Israeli Startups That Could Shape Our Future




Facebook comments