Israeli researchers at Check Point Software Technologies Ltd., a leading cybersecurity provider, revealed that hackers were able to steal $1 million from a Chinese venture capital firm earlier this year through a targeted business email compromise (BEC) scam. The money was intended for an Israeli startup.
In a detailed incident response case file this month, Check Point Incident Response Analyst Matan Ben David shared neither the name of the Chinese VC that was targeted nor the one of the Israeli startup that was supposed to be collecting the money as seed funding.
Neither party thought anything was wrong until the Israeli company realized it had not received the funds.
SEE ALSO: Israeli Researchers Discover Fortnite Flaw That Lets Hackers Take Over Accounts
“A Chinese venture capital firm was alerted by their bank that there was an issue with one of their recent wire transactions. A few days later, a young Israeli startup realized they didn’t receive their one million dollars seed funding,” Ben David wrote in the case file, “Both sides got on the phone and quickly realized that their money was stolen.”
As the companies realized the money was gone, they also noticed emails between the two parties that were altered and some correspondence that was fabricated.
It was at this point that they reached out to the Check Point incident response team about the money transfer and the Tel Aviv-based security firm began to go through emails, computers, and server logs.
The hackers had actually done more than just monitor the emails through an auto-forwarding maneuver as is usually seen in traditional BEC cases, Ben David wrote. Check Point said they had actually registered two lookalike domains — one which looked just like the Israeli startup, but which had an additional ‘s’ added to the end, and the other which looked like the domain of the Chinese VC, but also with an ‘s.’
The attacker sent two emails with the same headline as the original thread, with the first sent to the Chinese VC from the Israeli lookalike domain, through a spoof of the email address of the Israel startup’s CEO, according to the research. The second email was sent to the Israeli startup from the Chinese VC’s lookalike domain through a fake email address from the VC account manager handling the investment.
It’s a strategy that gave the attacker the ability to conduct the ultimate Man-In-The-Middle (MITM) attack, Ben David said.
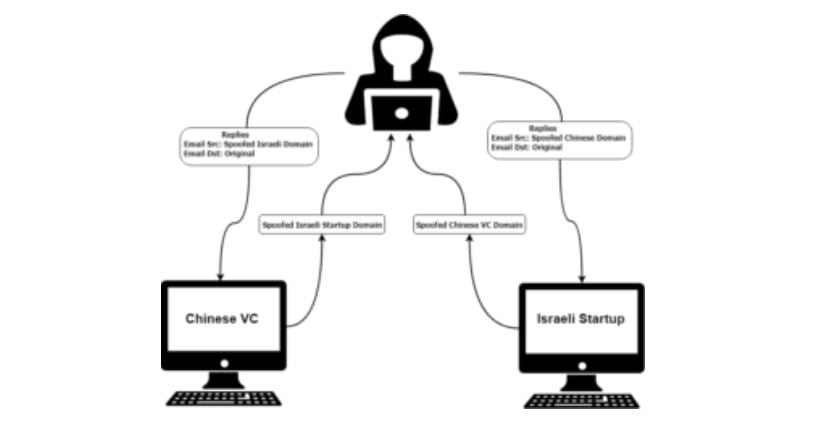
Every email sent by each side was actually sent to the attacker first, who then reviewed the email, decided if content needed to be modified and forwarded the email from the relevant lookalike domain to its original destination, according to the post.
Sign up for our free weekly newsletter
Subscribe“Throughout the entire course of this attack, the attacker sent 18 emails to the Chinese side and 14 to the Israeli side. Patience, attention to detail and good reconnaissance on the part of the attacker made this attack a success,” Ben David wrote.
The attack, which may have originated in Hong Kong, according to reports, successfully used the MITM strategy to scam the companies and steal funds. The attacker even went as far as sending emails to both parties to cancel a scheduled meeting in Shanghai, which had it occurred, would likely have thwarted the whole scheme.
The attacker, who has yet to be identified, took things further by asking for more money. The Israeli startup’s CFO continues to receive an email a month from the fake CEO account urging him to make a wire transaction, Ben David said.
SEE ALSO: Check Point Finds High-Risk Bug That Exposed DJI Drone Visuals, User Data
Check Point offered a number of ways to avoid situations like the one they discovered in a “Lessons Learned / Key Takeaways” portion at the end of the report. These include adding a second verification mechanism by calling the person or calling the receiving party to guarantee the transaction arrived at the intended party and ensuring email infrastructure is able to keep audit and access logs.
Above all, prevention is key, says Check Point. “Email is by far the number one vector for attackers to infiltrate business networks,” according to Ben David.
Phishing emails baiting users to expose organization credentials or click malicious link or files are “the number one threat in the email space.”
(The most famous case of this in recent history is the email hacking of the Democratic National Committee in 2016 and the subsequent event it unleashed.)
“Organizations must always incorporate an email security solution, designed to prevent such attacks automatically utilizing continuously updated security engines,” he wrote.
Related posts

Editors’ & Readers’ Choice: 10 Favorite NoCamels Articles

Forward Facing: What Does The Future Hold For Israeli High-Tech?

Impact Innovation: Israeli Startups That Could Shape Our Future




Facebook comments