WhatsApp, the wildly popular messaging platform owned by Facebook, has filed a lawsuit in a US court against Israeli cyber intelligence firm NSO Group, accusing it of being behind a malware attack earlier this year that targeted some 1,400 people across the world, including human rights activists and journalists.
In the claim filed in a district court in California where Facebook and WhatsApp are co-named as plaintiffs, WhatsApp says the cyber-espionage campaign was designed to infect the devices of the targets “for the purpose of conducting surveillance of specific WhatsApp users.”
NSO Group said in a statement sent to NoCamels that it disputes the allegations and “will vigorously fight them.”
In May 2019, WhatsApp announced that it detected and blocked sophisticated hacking attempts by “an advanced cyber actor” who “exploited a security flaw and installed the malware by targeting users’ mobile phones through WhatsApp’s call function,” the Washington Post reported at the time. The company called then on its 1.5 billion users to update the app to plug the security hole.
SEE ALSO: Israel’s Cyber Innovators Sign Off On Year Marked By Big Investments, Warn Of Dangers Ahead
WhatsApp did not name the actor at the time but said the campaign had the “hallmarks of a private company that reportedly works with governments to deliver spyware that takes over the functions of mobile phone operating systems.”

NSO Group has become infamous for developing a powerful, invasive piece of spyware called Pegasus that can access private data including passwords, web history phone call logs, contact lists, and text messages, and can monitor live calls from messaging apps. It can also turn on phone cameras and microphones to track events in the vicinity and use the GPS function to monitor a target’s location and movements.
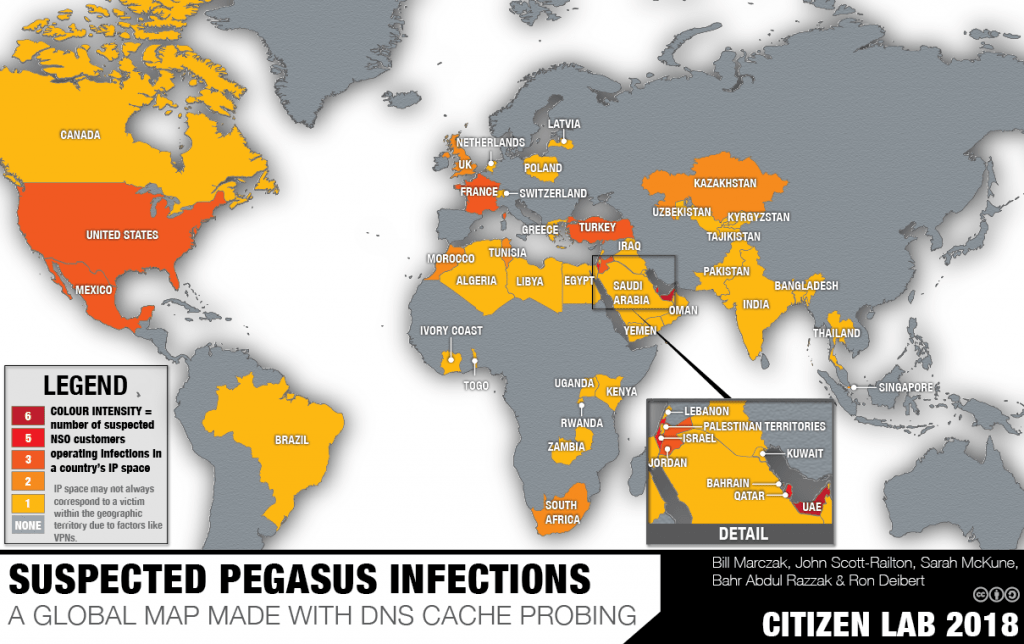
Though NSO claims its software makes the world a safer place “by providing authorized governments with technology that helps them combat terror and crime,” its tools have been linked to a number of high-profile cases including the 2018 murder of Washington Post journalist and Saudi Arabian dissident Jamal Khashoggi and the targeting of journalists and dissidents in Mexico and other countries, according to extensive research by Citizen Lab, a research facility at The University of Toronto’s Munk School of Global Affairs.

Citizen Lab said that among the many cyber companies it tracks as part of its work, NSO Group “stands out in terms of the reckless abuse of its spyware by government clients.”
“Although the technology is marketed as a tool to assist governments in lawful investigations into crime and terrorism, Citizen Lab has identified dozens of cases where journalists, human rights activists and defenders, lawyers, international investigators, political opposition groups, and other members of civil society have been targeted…”
In the WhatsApp attack, which the company says occurred in April-May 2019, NSO Group set up computer infrastructure and remote servers, as well as various WhatsApp accounts created by “employees and agents,” to target devices by initiating what appeared to be legitimate calls that were designed to secretly inject malicious code. The targets did not even have to answer the calls.
The “callers” had WhatsApp numbers with country codes from several countries, including the Kingdom of Bahrain, the United Arab Emirates, and Mexico.
In some cases, according to WhatsApp’s complaint, NSO Group caused the malicious code to execute on some of the target Devices, creating a connection between those devices and computers controlled by the Israeli firm “for the purpose of accessing data and communications.”
Will Cathcart, head of WhatsApp published an op-ed in the Washington Post on Tuesday directly accusing NSO Group of being behind the intrusion.
“We learned that the attackers used servers and Internet-hosting services that were previously associated with NSO. In addition, as our complaint notes, we have tied certain WhatsApp accounts used during the attacks back to NSO. While their attack was highly sophisticated, their attempts to cover their tracks were not entirely successful,” he wrote.
He also dismissed NSO’s denials, saying WhatsApp’s investigation, with the help of Citizen Lab, found otherwise.
“Now, we are seeking to hold NSO accountable under US state and federal laws, including the US Computer Fraud and Abuse Act,” he said.
WhatsApp said NSO Group was “unable to break WhatsApp’s end-to-end encryption,” and so “reverse-engineered the WhatsApp app and developed a program to enable them to emulate legitimate WhatsApp network traffic in order to transmit malicious code—undetected—to Target Devices over WhatsApp servers.”
Cathcart said the investigation unearthed another “disturbing pattern to the attack,” targeting at least 100 human-rights defenders, journalists and other members of civil society across the world.”
Cathcart said the incident should “serve as a wake-up call for technology companies, governments and all Internet users.”
“Tools that enable surveillance into our private lives are being abused, and the proliferation of this technology into the hands of irresponsible companies and governments puts us all at risk,” he warned.

WhatsApp’s lawsuit says NSO’s actions burdened its network, injured its reputation, public trust, and goodwill, and caused “damages in excess of $75,000,” in addition to any amount proven at trial. That amount was not specified.
The company also called on the court to issue a permanent injunction barring NSO Group, and anyone affiliated with it from accessing Facebook or WhatsApp’s service and computer platforms.
NSO Group has rejected the allegations. “In the strongest possible terms, we dispute today’s allegations and will vigorously fight them,” the company said in a statement.
“The sole purpose of NSO is to provide technology to licensed government intelligence and law enforcement agencies to help them fight terrorism and serious crime. Our technology is not designed or licensed for use against human rights activists and journalists. It has helped to save thousands of lives over recent years,” the group said.
“The truth is that strongly encrypted platforms are often used by pedophile rings, drug kingpins and terrorists to shield their criminal activity. Without sophisticated technologies, the law enforcement agencies meant to keep us all safe face insurmountable hurdles. NSO’s technologies provide proportionate, lawful solutions to this issue,” the company added in the statement.
Sign up for our free weekly newsletter
SubscribeIn May, Amnesty International filed a petition with the Tel Aviv District Court to demand that the Israeli Ministry of Defense (MoD) revoke NSO Group’s export license.
Amnesty International said one of its researchers was targeted by NSO Group in June 2018.
“NSO Group sells its products to governments who are known for outrageous human rights abuses, giving them the tools to track activists and critics. The attack on Amnesty International was the final straw,” said Danna Ingleton, deputy director of Amnesty Tech, who provided supporting testimony.
“The Israeli MoD has ignored mounting evidence linking NSO Group to attacks on human rights defenders, which is why we are supporting this case. As long as products like Pegasus are marketed without proper control and oversight, the rights and safety of Amnesty International’s staff and that of other activists, journalists and dissidents around the world is at risk,” she said.
What is NSO Group?
NSO Group was founded in 2009 by Niv Carmi, Omri Lavie, and Shalev Hulio – their names form the initials NSO. Carmi left the company years ago but the name remained.
It has offices in Israel and the US and has gone by different names, including Q Cyber Technologies (named in WhatsApp’s claim as a defendant), which was initially incorporated as L.E.G.D. Company. OSY Technologies S.A.R.L. has been named as the only Q Cyber shareholder and active director.
The firm rose to prominence first in 2016 when it was discovered that its software was used to hack into the phone of Ahmed Mansoor, a United Arab Emirates human rights activist.
Mansoor received a text message offering to provide information about tortured detainees in the UAE if he clicked on a link in the message. Suspicious. He alerted Citizen Lab, which traced the technology back to the NSO Group and has been monitoring it since. Had Mansoor clicked on the link, the organization using the Pegasus software (suspected to be the UAE government) would have had full access to the activist’s phone.
In 2017, Citizen Lab released a report that said the software had also been deployed in Mexico where 76 text messages were sent to targets including lawyers investigating the disappearance of 43 students, influential journalists, an anti-corruption academic, and a minor child of a journalist. Many of the text messages impersonated legitimate organizations.
That same year, an Android version of the Pegasus malware (termed ‘Chrysaor’) was discovered. Google’s Vice President of Security Intelligence Mike Murray commented that Chrysaor was “one of the most sophisticated and targeted mobile attacks we’ve seen in the wild.” Google identified targets of the software located in Israel, Georgia, Mexico, Turkey, and the UAE.
And in the most famous and gravest case, in 2018 Citizen Lab unveiled that a close confidant of Khashoggi, also a Saudi dissident, was targeted by the Saudi government in Canada with a fake package notification, resulting in the suspected infection of his iPhone. It is believed that Khashoggi’s correspondence with Omar Abdulaziz was intercepted and was used to track Khashoggi before his murder at the Saudi embassy in Istanbul on October 2, 2018.
Abdulaziz, 28, lodged a civil case against NSO Group in Tel Aviv in December 2018.
NSO Group had remained silent on all allegations until after information surfaced that its tools may have been used to ensnare Khashoggi, after which it issued a sharp denial.
“I can tell you very clear[ly], we had nothing to do with this horrible murder,” Hulio said in an interview with 60 Minutes aired in March.

Months prior, Hulio told Israeli investigative journalist Dr. Ronen Bergman in a January 2019 interview with Yediot Ahronot that NSO “conducted a thorough inspection of all of our clients, not just the one client who could perhaps be a potential suspect for involvement in the affair, but also other customers who may for some reason have had an interest in monitoring him.”
“We also checked whether maybe someone went to a certain other country and asked their intelligence services ‘to do him a favor.’ We checked all of our clients, both through conversations with them and through technological testing that cannot be forged. The systems have records and it is impossible to act against a target such as this without us being able to check it,” Hulio said.
“After all these tests, I can tell you, in an attributed quote, that Khashoggi was not targeted by any NSO product or technology, including listening, monitoring, location tracking, and intelligence collection,” he said.
Hulio explained that NSO Group’s clients, governments that acquired its technologies, “are very limited in the number of targets they can actually handle. In the entire world, there are today no more than 150 active targets.”
“This, along with well-secured cell phone operating systems and advanced application security, dramatically reduces the possibility of tracking civilians who are not involved in terrorist or criminal acts,” Hulio said.
SEE ALSO:Spy Games: Ex-Mossad Chief’s Cybersecurity Startup Counters Attacks With A Hacker’s Mindset
The Yediot piece also alludes to cases where NSO’s tech was used to stop a suicide bombing, disrupt a pedophile ring, and help capture a notorious drug cartel leader, and map recruitment efforts by the Islamic State terror group
Since the company was founded, Hulio said, “tens of thousands of lives have been saved thanks to foiled terror attacks and crimes, scores of abducted children have been returned to their parents, survivors have been found in the wreckage of buildings, and extremely serious crimes have been prevented.”
The NSO co-founder alleged that the company can track and monitor how its technology is used and does not shy away from pulling the plug when it identifies violations.
When asked by 60 Minutes if NSO’s alleged ties with Saudi Arabia were terminated after the murder of Khashoggi, Hulio refused to answer.
“I’m not gonna talk about…We do what we need to do. We help create a safer world,” he insisted.
Related posts

Editors’ & Readers’ Choice: 10 Favorite NoCamels Articles

Forward Facing: What Does The Future Hold For Israeli High-Tech?

Impact Innovation: Israeli Startups That Could Shape Our Future




Facebook comments