As the world increasingly moves to cloud-based digital operations, an Israeli startup is protecting companies from hackers, phishers and other cybercriminals by intercepting would-be malicious attacks directed at their personnel long before they even reach them.
Today, everything operates in the cloud, from email to apps and even browsers, which presents its own unique security challenges, Perception Point Chief Marketing Officer Karen Krivaa tells NoCamels.
“The workspace has changed, and this gives attackers lots of places and lots of gaps to get to the user and send malicious either files or links or even text,” Krivaa says.
Perception Point focuses on these different channels in the modern workspace, protecting the user in the areas of email, browser and app security from one platform, with just one interface that also operates from the cloud.
“It’s a SaaS [software as a service] solution; it’s cloud,” Krivaa says.

The platform functions through an API (application programming interface), a piece of software that allows two or more digital devices to talk to one another, weeding out potential threats, and, in the case of emails that form around 90 percent of malicious attacks, before they even arrive in the user’s inbox.
Any suspicious email is immediately quarantined and inspected before it is passed along to the recipient. If malicious, it never reaches the user.
Email servers can easily connect to the Perception Point platform, usually in just “three clicks,” Kirvaa says, while browsers connect through a URL. This allows the platform to scan every incoming piece of data for malicious activity.
“Everything is already built in,” according to Kirvaa.
The platform conducts what the Perception Point calls its own unique dynamic scanning service, examining every piece of data incoming to a business’ servers and network to determine whether it has a sinister intent, creating a layer of protection that swings into action before the servers can pass the data on to the intended recipient.
The software significantly relies on AI automation to root out the potential threats, but Krivaa says that there is also an active human component, with cybersecurity experts constantly reviewing the platform to ensure that nothing slips through the cracks. And if it does, the company immediately takes action to mitigate the threat.
“Nothing is 100 percent perfect,” she says. “If something gets through, we remediate it right away.”
And, Krivaa says, the company does not rely just on finding threats that have already been identified in the cybersecurity world, but understands that every day brings new methods of attacking businesses.
“We actually scan, check every single link, every single file,” Krivaa says. “It could be a new type of malware never seen before; it could be a new phishing site never seen before.”
Krivaa explains that hackers and other cyberattackers are becoming exponentially more sophisticated, even to the point of being able to find pre-prepared packages that they can adapt to strike at companies.
“Attackers are using GenAI,” she says, referring to artificial intelligence programs that allow users to create all kinds of media from text and images to videos using simple prompts.
“They [created] attack as a service,” she says. “You can buy phishing kits, input your stuff and you’re ready to go.”
Sign up for our free weekly newsletter
SubscribeThis level of refinement can be problematic for what Krivaa calls “legacy” cybersecurity companies, which she says cannot cope with the rapid shift in both the proliferation and the sophistication of modern attacks.
In fact, it was Perception Point that alerted the world to the recent highly sophisticated phishing attack that the company dubbed “Uncle Scam” as it originated from an email posing as a US government account.
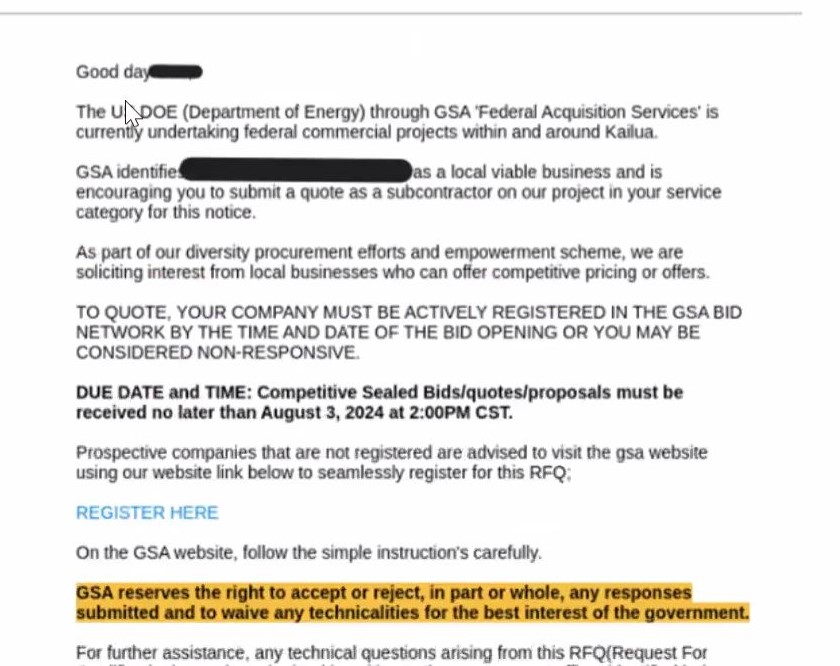
Adding credence to the phishing scheme was the fact that the people behind the email account used the domain of Microsoft’s Dynamics 365 marketing platform, which organizations regularly use for various business purposes and which may have helped the emails sneak past other security measures.
The email claimed to be from the General Services Administration (GSA), asking the recipient to bid on a Department of Energy project, and the link within led to a spoofed website that had every detail of the original perfectly copied.
Every link on the cloned website worked, adding to the image of authenticity, Krivaa says, and ultimately it led the visitor to a form to provide confidential details such as usernames and passwords.
“The more you go into it and the more reliable it seems, the more you trust it,” Krivaa says. “It was really scary. A lot of work went into this.”
Another recent phishing attempt with a similar level of sophistication that Perception Point rooted out was one that capitalized on the outage of the CrowdStrike cybersecurity company in July, when a botched software update caused millions of systems worldwide that use Windows to crash.
The phishing attempt involved the email account update@crowdstrike.com.vc, claiming to be from CrowdStrike and with a domain name that looked legitimate. Only the easily overlooked “vc” at the end of the address indicates that this was not from the company itself.
“They took advantage of the Crowdstrike error, and they swung into action,” Krivaa says of the email, which included malware purporting to be able to correct the original botched update.
Perception Point’s system isolated the zipped file placed inside the PDF that was attached to the email. And inside the zipped file was an executable file called CrowdStrike.exe, which, Krivaa says “basically wipes out your entire computer.”
The latter attack, she says, likely originated in Iran.
Tel Aviv-based Perception Point was set up in 2015 by IDF cybersecurity veterans, who started with a platform that could identify specific malware that had never been seen before.
From there, the company expanded to a wide range of cybersecurity protection and today services more than 8,000 companies (it is a strictly B2B operation) of varying sizes across the globe.
Krivaa says that working for a cybersecurity company has taught her to be suspicious of every email she receives to her personal account, and warns that others should be just as vigilant.
“I never click on anything,” she says. “If I get a message, I go to my laptop, I go to the company site, I log in, and that’s how I check.”
Related posts

Editors’ & Readers’ Choice: 10 Favorite NoCamels Articles

Forward Facing: What Does The Future Hold For Israeli High-Tech?

Impact Innovation: Israeli Startups That Could Shape Our Future




Facebook comments